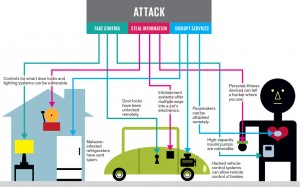
Vulnerabilities of Internet of Things
Internet of Things (IoT) will be one of the most important technology in today’s and tomorrow’s world. With this key technology, there will be many areas that will affect from the internet of things. The benefits of Internet of Things will be more than expected. But how about the security?
Beside the benefits of Internet of Things (IoT) , it will cause huge security vulnerabilities. Innocent refrigerator can be a backdoor for malicious network attacks of hackers.
We can give a lot of real world examples to internet of things vulnerabilities. One fo them is about a connected car control. In July 2015, a connected car hacked by hackers and controlles remotely. Hackers entered this connected cars network and control air conditionning, radio frequencies etc. How about they tried to control the root the car? These can cause very harmfull usages and maybe because of such malicious attacks, people can die or badly affected.
Another example had seemed in the oil pipeline control of Turkey at 2008. Hackers entered the oil pipeline system and they changed the temperature of pipeline and blew up the pipeline. Hackers had entered this oil pipeline from the security webcams. Can you imagine the badly affacted of internet of things if you do not secure it completely?
There can be many security vulnerabilities. Researchers are currently working on it and many Internet of Things tests are being done. In this article, we will foxus on the key vulnerabilities of Internet of Things. So what is these vulnerabilities and how can you protect your internet of things network from the malicious things? Here is the list of Internet of Things Vulnerabilities:
Devices That Seem Innocent
The most important part is the devices that seem innocent. Your security web cam, your refrigerator, your air conditioning system, even if your smoke detector are all these category. These devices are producet for todays’s world and many of them has too much vulnerabilities on security. These devices are not secure for internet of things and so any malicious person can enter your house network, by firstly entering your innocent looking devices.
What to do?
To avoid this harmful affect of the security vulnerabilities of internet of things, first you need to detect all of your devices connected to your network.There are many network discovery tools for this. You can detect these devices by yourself or you can hire a company for this first security step. Here, our motto is “you can not secure against, if you do not know if there is such a device in your network”.
Outdated Softwares and Antivirus Programs
Attackers generally use the vulnerabilities of the softwares. These vulnerabilities are always patched by the developers when they realized. So, to protect your network, you device’s softwares always need to be updated. Your antivirus programs also need to be updated to the new viruses and attack types.
What to do?
To avoid this harmfull affects, control your devices softwares, antivirus programs and update them periodically. Here, our motto is “be ready for viruses”.
Weak Passwords
People generally use very weak password because of the fact that they do not want to forget it. but, using weak passwords is one of the things that you must not do if you want to protect your internet of things network. Think about it? Your iar conditionning mechanism is online. If you give your birthday date as a password, is it secure? Anybody can easily guess this value.
What to do?
Use strong passwords for the devices in you internet of things network. Using upper and lower cases, numbers and alfa numeric values together can be better. Here, our motto is “try to remember as more strong password as you can”.
Unnecessary Information Share
The smart devices in your Internet of Things network are under your control. They know what you give to them. So, unnecessary information share with your smart devices is not a good behaviour. Because, if a malicious atatck occurs, somebody can easily learn this information.
What to do?
Share less information with your smart device. Your personal information etc. must not be in your smart devices.Here, our motto is “do not share your birthday with your device”.
Putting all thing eggs into the same basket
In your house or company, you use Wi-Fi that provide you to connect to the internet. Beside this, you will also have your internet of things network. Having only one network can be dangerous. because if an hacher enters inside, then all of your connected devices can be controlled.
What to do?
Seperate your network into smaller portions. Especially do not put your internet of things devices in to the same network with your Wi-Fi. Here, our motto is “seperate baskets are better”.
External Backdoors
To secure your Internet of Things network, one of the most important behaviour is locking down the external connections to your network. Most atackes came from outside. So your door need to be locked for others.
What to do?
Lock down all external connections to your networks. Allow only the people that has enough access rights. Here, our motto is “doors close to the others”.
Noexpert People
In companies generally there is structure that includes different departments. So, to buy a new device, generally buying process is controlled by the people who are not expert on security.
This seperation must be done better in the future world because of Internet of Things.
What to do?
When an Internet of Things device need to be bought, a security expert must analyze and select this device. By doing this, the vulnerabilities become less. Here, our motto is “everyone needs to do its job”.
Weak Security Standards
You network must be consist of the devices that has strong security standards . You must not allow a device into your network that has not a certain security standards.
What to do?
When you buy a new device into your Internet of Things network, be careful about its security standards and be sure that it will not cause a backdoor in your network. Here, our motto is “standards are important”.
Weak Access Rights
People has access rights to the devices that they live around. Your home, your company, your store etc. There can be many people inside the buildings and all of them use different devices of this Internet of Things network. All these people must have enought but not much access rights to the devices. If you give to much access rght to a person, this can cause a bad affect into your network.
What to do?
Plan your network access rights and do a people list for your Internet of Things devices. Avoid unnecessary access rights.Here, our motto is “everyone has its own rights”.
Beside these vulnerabilities, Internet of Things has other vulneraiblities. Day by day these are coming in front of us. To become a secure actor in Internet of Things world you need to secure your network an be carefull about these new security areas.